When you want to enable MultiFactorAuthentication (MFA) for Azure / Intune / Office 365 / Dynamics 365 and you are using federated logins and want to have the MFA provider to be on-premises (integrated with ADFS/PingFed/other) integrated.. you might run into an issue where the Azure MFA page keeps popping-up and asking you to register your account instead of using your own MFA provider.
By default, when you switch to an on-premises MFA service, you need to “tell” Office 365 that you have an MFA capable Federation Service ready. To do this, you run the following command from the MSOL PowerShell commandlets
Set-MsolDomainFederationSettings -DomainName <name.com> -SupportsMFA $true
This should do the initial trick and enable the MFA for on-premises.. however.. in some cases the above is not enough.. Despite the -SupportsMFA=true value, all users are still getting the Azure MFA prompt which is not what we are trying to achieve
To fix this issue, we need to look at a specific attribute by requesting the current federation settings for your domain:
Get-MsolDomainFederationSettings -DomainName <name.com>
and look for the following attribute: PromptLoginBehavior
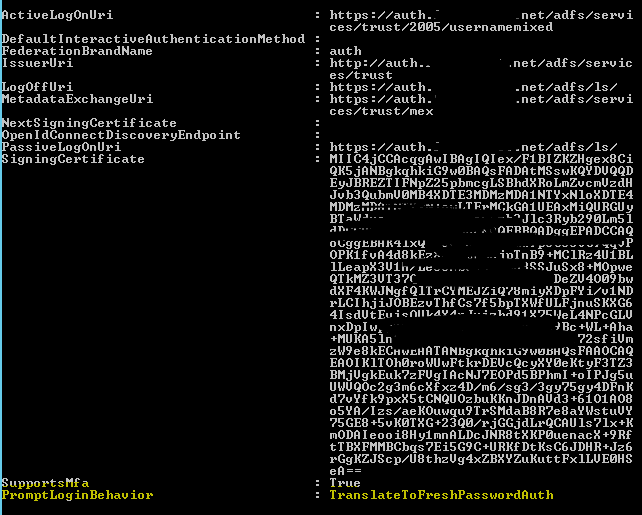
If this value is not present in your get-MsolDomainFederationSettings command, it means we can update it by issuing the following command:
Set-MsolDomainFederationSettings -DomainName <name.com> -PromptLoginBehavior TranslateToFreshPasswordAuth
Now the question is obviously what does this option do?
It is an attribute that has been added when ADFS 2016 came out and when more and more applications with modern authentication enabled became available, the platform needed to be able to control the login behaviour. These applications convert the authentication into two parameters: wauth=….. and wfresh=…
For the values there are 3 options:
- TranslateToFreshPasswordAuth
- NativeSupport
- Disabled
The TranslateToFreshPasswordAuth one is the default one, the wauth parameter when MFA is requested, will be set to wauth=http://schemas.microsoft.com/claims/multipleauthn
If you use a 3rd party proxy service that needs to filter based on the URL, the multipleauthN parameter will do nicely..
If your PromptLoginBehavior is not present in the Get-MsoldomainFederationSettings overview, and you are using ADFS 2012R2 / 2016, set it to TranslateToFreshPasswordAuth
The option NativeSupport means that the prompt=login parameter will be sent 1:1 to the Federation service.
and the Disabled means nothing will be sent to ADFS (and thus no MFA will be triggered)
Important: in some cases when you change either PreferredAuthenticationProtocol, SupportsMFA or PromptLoginBehavior you will need to set all three options as each of them can be reset to default when changing another value.
Only in certain conditions (read non ADFS servers) do you need to set the PreferredAuthenticationProtocol to Samlp. When using ADFS you can set it to:
Set-MsolDomainFederationSettings -DomainName -PreferredAuthenticationProtocol WsFed
And that’s it.. while it may take a few minutes to become active, on-premises MFA should be enabled!
Applies to: ADFS 2012R2 with July 2016 update & ADFS 2016
More info: https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/overview/ad-fs-faq
