In my previous post I talked about FIDO2 keys from FEITIAN and how to register them. One of the points for registration was that you need to sign-in with MFA to register your FIDO2 key. But what if your users do not want that, or cannot do that?
To the rescue comes ENSURITY. They have a solution for this in the form of the software that comes with their hardware FIDO2 token – the ThinC-AUTH.

The device itself is a bit bigger than the FEITIAN BIOPASS, but as the sensor sits a bit higher it reads your fingerprint much faster. With the Biopass I need to adjust my fingers continuously, with the ThinC I did not have to do that yet. The bulkiness of the key however is undeniable. If needed however (and thats a big plus for them), you can purchase the ThinC-Vault. An encrypted USB storage device with FIDO2 support as well. The only thing I’m a bit worried about is all the plastic on the key, especially the ring holder. It would be easier to break under stress and in the really, really hot environment I live in, plastics don’t hold on too long.

So, apart from the key review, we will be looking at the software mostly that allows us to register our key without any prior MFA mechanism available.
The software
First you will need to download the software from their website https://ensurity.com/Products/ThinC_AUTH#Resources. I chose the Windows version but there is support for other operating systems as well. After installing the software and running it (unfortunately you need local admin rights), you need to plug in the key you want to use and select it.
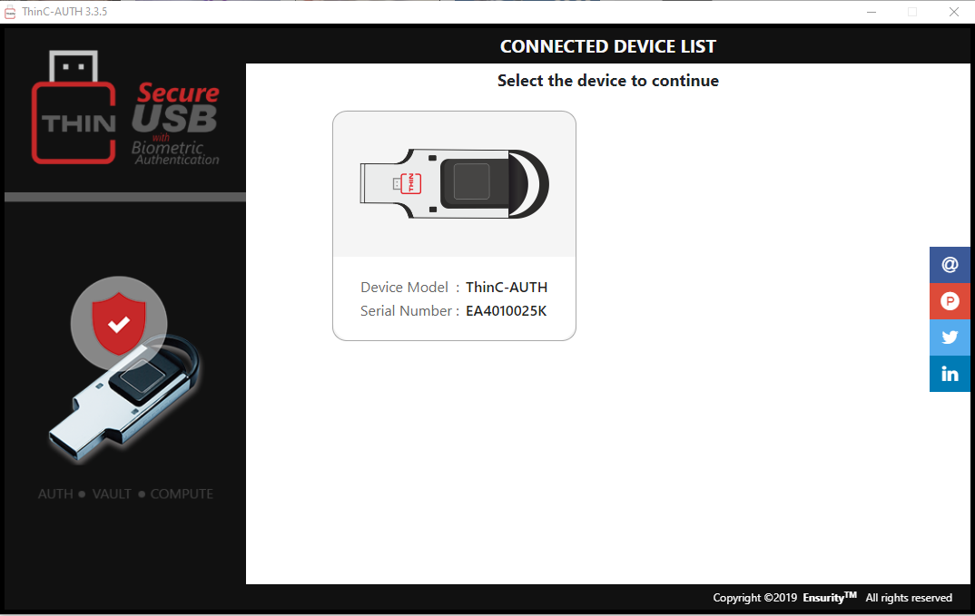
Click the device and set a Security PIN. And after that you can enroll a fingerprint to the device.
In principle the device is ready now for onboarding to Azure AD or other identity providers supporting FIDO2.
OATH-OTP / TOTP
In this scenario I have a brand-new user without any MFA provider specified. When the user logs in using regular username and password a pop-up will be shown asking the user for add additional verification methods:
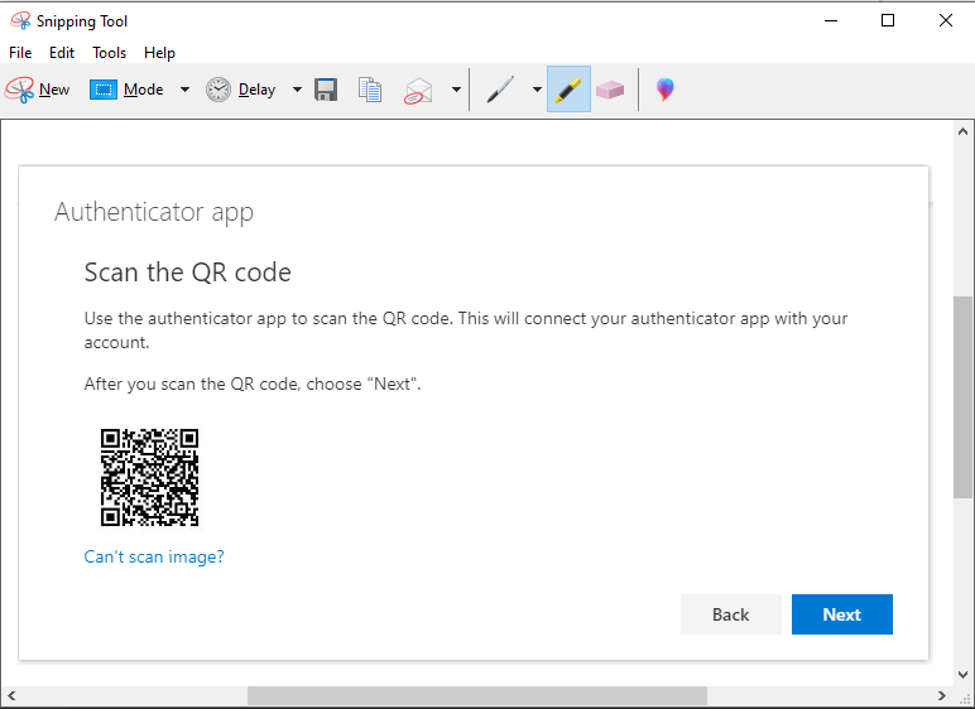
Save the image file and then go to the ThinC-Auth software and select the OATH-HOTP/TOTP tab in the top. Click + to register a new authentication and click Choose file to browse to the earlier saved file.
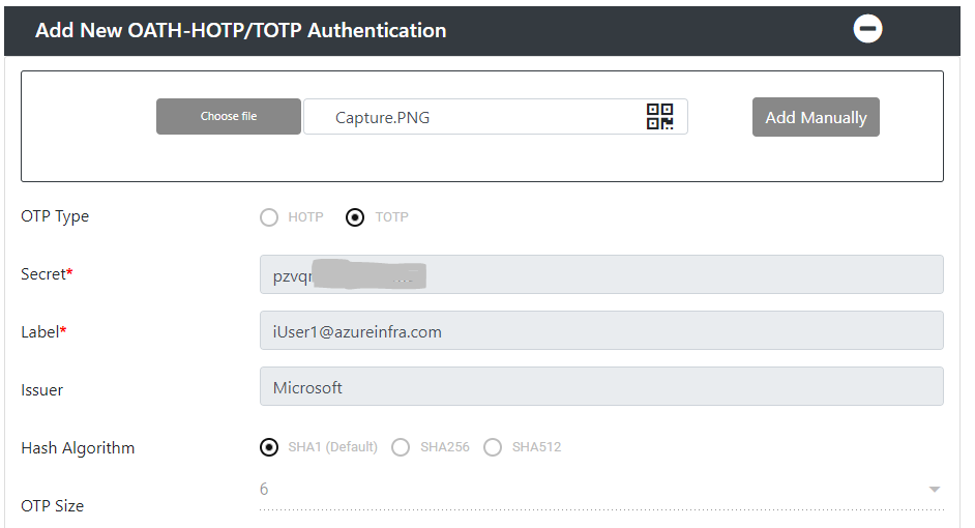
The image will be read, and the application will fill in the Secret, the Label and Issuer. Click Update and provide the PIN to the key.
Go back to the browser and click next on the QR image window. The browser window will ask for a 6 digit code. This code can be provided by the Ensurity software.
On the main page, click Get Secret TOTP and touch the security key go generate it. Copy the 6 digit code and paste it in the browser to gain access.
We have now competed the “Authenticator” setup for our account. Next, we can enroll the FIDO2 key itself using the regular (and previously described) method.
Conclusion
While Microsoft will encourage you to use the Microsoft Authenticator app, as it’s registration and use is much simpler, you can also use alternative methods to provide 2-Factor authentication. These include (although not described here) the Google Authenticator, or other 3rd party token providers. In this case Ensurity used that possibility to build the TOPT generator in a software package and combine it with the use of their keys for security.
The end-goal however is the same. We can now safely register the key as TOTP provider in combination with the software and use the same key after FIDO2 registration for passwordless authentication.
Now, you might be like me, I always forget my FIDO2 keys, don’t want them on my key chain as my Volvo key is so big it wouldn’t be good for my USB port .. isn’t there a better way? Yes, there is… seems I need to get myself an Android phone soon…